What is TLS?
TLS (Transport Layer Security) is a security protocol used to establish a secure communication channel between two computers over the Internet. It is the successor to the earlier SSL (Secure Sockets Layer) protocol and is used to ensure the privacy and integrity of data transmitted over the Internet. TLS is commonly used in web browsers to encrypt data that is exchanged between a website and a user's computer. It is also used in other applications such as email, instant messaging, and virtual private networks (VPNs).
TLS (Transport Layer Security) is a security protocol used to establish a secure communication channel between two computers over the Internet. It is the successor to the earlier SSL (Secure Sockets Layer) protocol and is used to ensure the privacy and integrity of data transmitted over the Internet. TLS is commonly used in web browsers to encrypt data that is exchanged between a website and a user's computer. It is also used in other applications such as email, instant messaging, and virtual private networks (VPNs).
What are encryption algorithms?
Encryption algorithms are mathematical formulas used to convert plaintext (unencrypted data) into ciphertext (encrypted data) in a way that makes it difficult for unauthorized parties to read or decipher the original message. There are many encryption algorithms available, each with their strengths and weaknesses. Some of the most common encryption algorithms include Advanced Encryption Standard (AES), Data Encryption Standard (DES), and Rivest-Shamir-Adleman (RSA). When using encryption, the plaintext is encrypted using an encryption key, and the resulting ciphertext can only be decrypted back to plaintext using the corresponding decryption key.
What are cipher suites?
A cipher suite is a set of encryption algorithms and protocols used for establishing a secure communication channel between two computers over the Internet. It includes algorithms for key exchange, encryption, and message authentication. When two computers establish a secure connection using a protocol like TLS, they negotiate a cipher suite that they will use for the communication. The cipher suite determines the strength of the encryption used for the communication and the algorithms used to authenticate the message. Different cipher suites offer different levels of security and may be suitable for different use cases. The set of cipher suites supported by a server can affect which clients can communicate with it, as some clients may not support certain algorithms or protocols.
Which versions of DocuWare Cloud and related client software will support the new cipher suites?
Starting with DocuWare 7.7, we will no longer support weak Cipher Suite. They will be removed. This affects all software or services related to DocuWare, starting with DocuWare version 7.7
Which versions of the DocuWare Cloud SDK will support the new cipher suites?
Starting with DocuWare 7.7, we will no longer support weak Cipher Suite. They will be removed. This also impacts our SDK (Software Development Kit) starting with DocuWare version 7.7.
Will all operating systems and browsers be able to support the new cipher suites?
The supported environments are listed in our official help, which can be found here: https://help.docuware.com/#/home/82276/2/2
Will I still be able to access DocuWare Cloud if I'm using an outdated version of Windows or an old browser?
Clients, such as those using an old version of Windows or an old browser, may not be able to communicate with the DocuWare Cloud server if they do not support the new cipher suites. Therefore, if you are using an old version of Windows or an old browser that does not support the new cipher suites, you may not be able to access DocuWare Cloud. It is recommended that you ensure that you are using a supported operating system and browser to ensure compatibility with the new cipher suites and continue accessing DocuWare Cloud.
What should I do if I'm using customized integrations with the DocuWare Cloud SDK?
Customized integrations using the SDK or tools provided by partners or third parties should support the cipher suites listed in the new set of server-side security settings. Therefore, if you are using customized integrations with the DocuWare Cloud SDK, you should ensure that they are compatible with the new cipher suites. This may involve updating your integrations to use the new cipher suites, or contacting your partner or third-party provider to ensure that they are aware of the changes and are taking steps to ensure compatibility. Failure to update your customized integrations to support the new cipher suites could result in communication issues with the DocuWare Cloud server.
Where can I see which version of DocuWare I'm using?
You can see which DocuWare version you are using by clicking on the dropdown arrow underneath your user name of the Web Client. From here, go to About DocuWare, where this information will be shown
How can I see my HTTPS Handshakes in Fiddler?
You can easily use Fiddler to evaluate what algorithms a client is using to connect to an HTTPS server in Fiddler.
First, adjust Fiddler’s configuration using Tools > Fiddler Options to enable Capture HTTPS CONNECTs tunnels but disable Decryption HTTPS traffic.
You can easily use Fiddler to evaluate what algorithms a client is using to connect to an HTTPS server in Fiddler.
First, adjust Fiddler’s configuration using Tools > Fiddler Options to enable Capture HTTPS CONNECTs tunnels but disable Decryption HTTPS traffic.
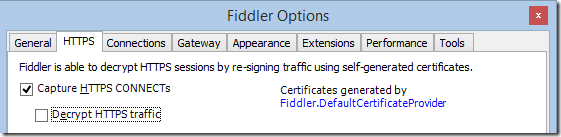
Disabling decryption is necessary because Fiddler decrypts traffic using an HTTPS man-in-the-middle technique, which means that when it’s enabled you’ll see what the client and server are using to talk to Fiddler, which could be different from what they’d use if Fiddler were not in the middle.
After making this change, load an HTTPS site inside your browser, and double-click on any of the CONNECT tunnel entries shown in Fiddler.
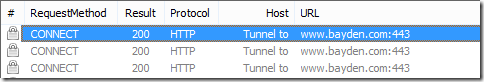
Fiddler’s TextView Request Inspector will show you a parsed view of the Client’s HTTPS handshake: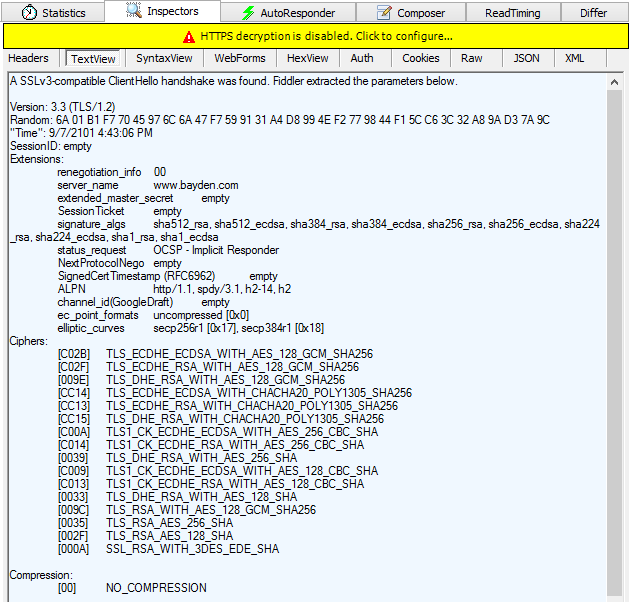
… and the Text View Response Inspector below will show the parameters chosen by the server for the connection: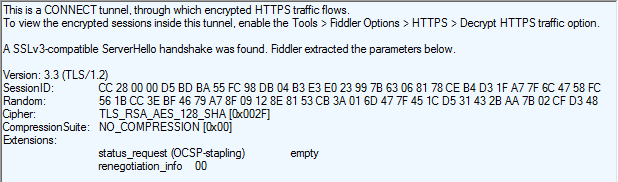
In this case, you can see that the Server agreed to a TLS/1.2 connection using RSA for key exchange and 128-bit AES as the symmetric encryption algorithm. The server ignored the ALPN extension, indicating that the connection will not be using HTTP2 or SPDY for data transfers.
Fiddler will show you exactly what your client and server agreed upon.


