Important Note:
Sending Windows credentials over the network can potentially be read by third parties if the network has not been adequately protected. For this reason, any part of this article that is not part of a DocuWare configuration file should always be approved and carefully customized by your security department.
Problem:
Sending Windows credentials over the network can potentially be read by third parties if the network has not been adequately protected. For this reason, any part of this article that is not part of a DocuWare configuration file should always be approved and carefully customized by your security department.
Problem:
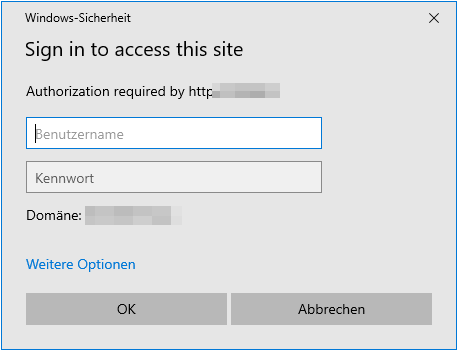
The Windows NTLM identity provider was configured as the single sign-on connection.
However, the Windows login window always appears. What must be done to authenticate a user via NTLM?
However, the Windows login window always appears. What must be done to authenticate a user via NTLM?
Answer:
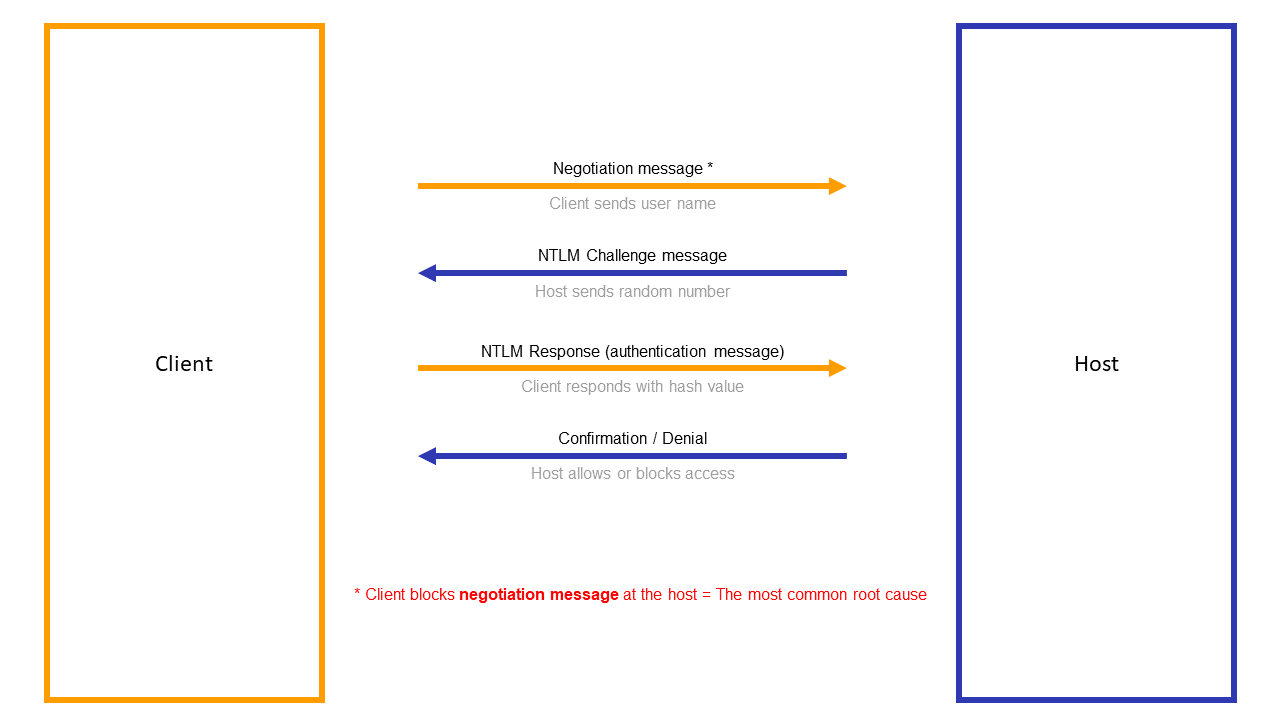
The Windows logon takes place via the NTLM protocol and is negotiated between the client (DocuWare user PC) and the host (server on which DocuWare is hosted). See Screenshot of this Challenge Response Mechanism.
DocuWare itself waits during this process for approval from the host on whether the client is allowed to see the resource or not.
NTLM works by default only for intranet sites, but HTTPS is not recognized as an intranet site from experience.
DocuWare itself waits during this process for approval from the host on whether the client is allowed to see the resource or not.
NTLM works by default only for intranet sites, but HTTPS is not recognized as an intranet site from experience.
The following requirements must be met to use NTLM.
- Browser
The browser is allowed to transfer the windows username to the host:
Location: Clients Computer
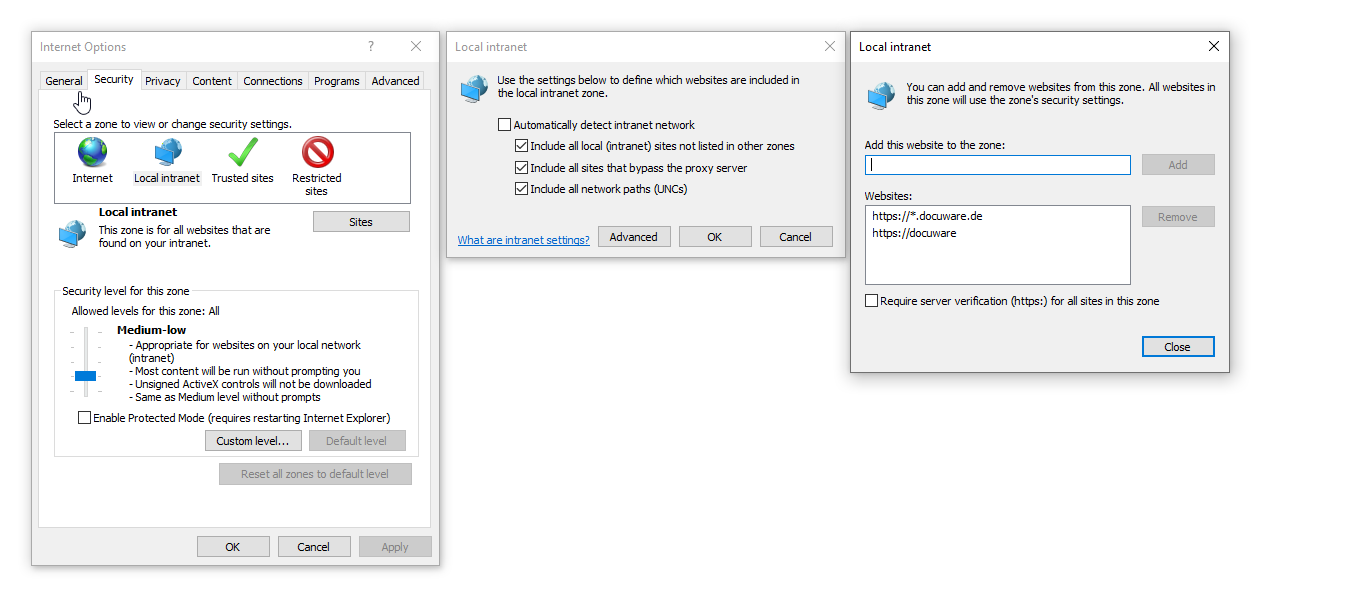
Edge, Chrome: (Internet Options > Security > Local intranet > Customize level: User Authentication - Automatic login with username and password. Furthermore, the DocuWare website (a*) should be added to the local intranet zone.
See Screenshot
Edge extra: By default, Microsoft Edge uses the intranet zone as an allowlist for Windows Integrated Authentication (WIA). Alternatively, you can customize the list of servers that are enabled for Integrated Authentication by using the AuthServerAllowlist policy.
https://learn.microsoft.com/en-us/deployedge/microsoft-edge-security-identity
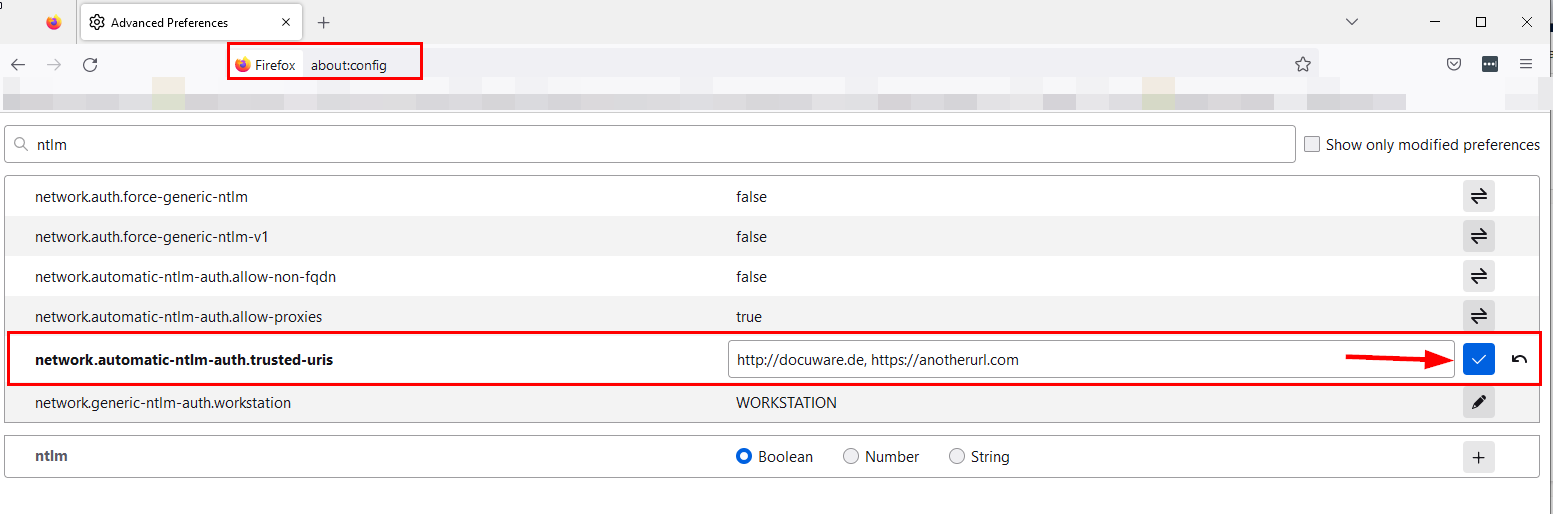
Firefox: about:config > network.automatic-ntlm-auth.trusted-uris > Here the DocWare web page (a*) is entered.
See Screenshot
a* For all browsers: The URL with protocol is entered here. If DocuWare is called via https://docuware.de/DocuWare, the value is https://docuware.de.
- Client
The client is allowed to transfer the Windows ID to the host
Location: Clients Computer
Windows prevents reflection attacks by default=
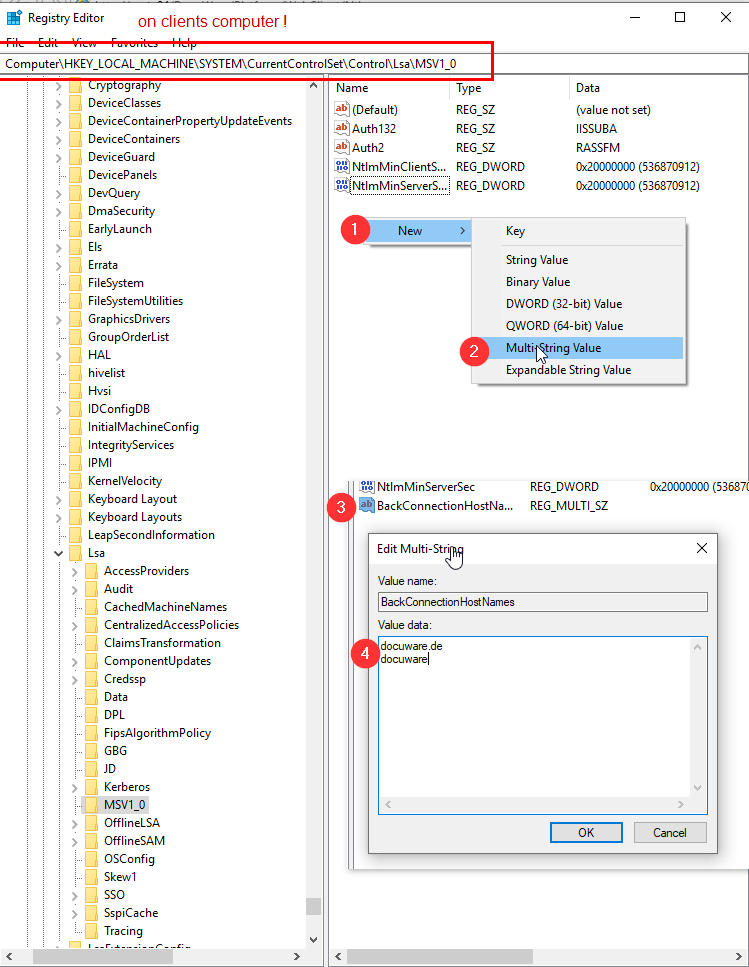
(b*) A key must be entered into the registry. This defines to which host the Windows ID may be transferred.
Registry path on the client: Computer\HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa\MSV1_0
Key type: multi-string value
Key name: BackConnectionHostNames
Key content: Any URL (without https protocol and without path). If DocuWare is called via https://docuware.de/DocuWare, the value is docuware.de
See Screenshot
- Network ID
The DocuWare User has the correct network id (Windows User ID)
Location: /DocuWare/Settings/
- Identity Provider
NTLM is chosen as SSO Login Method.
Location: /DocuWare/Settings/
b* we recommend talking to your IT-Security first because you send windows credentials over the network, which can be insecure.
- WIA-based SSO with ADFS
To support WIA-based SSO on Microsoft Edge (version 77 and later), you might also have to do some server-side configuration. You'll probably have to configure the Active Directory Federation Services (AD FS) property WiaSupportedUserAgents to add support for the new Microsoft Edge user agent string
External sources of information:
https://learn.microsoft.com/en-us/deployedge/microsoft-edge-security-identity
https://www.crowdstrike.de/cybersecurity-101/ntlm-windows-new-technology-lan-manager/ (german)
https://www.crowdstrike.com/cybersecurity-101/ntlm-windows-new-technology-lan-manager/ (english)
https://www.crowdstrike.com/ search for NTLM to find further blog articles from this website
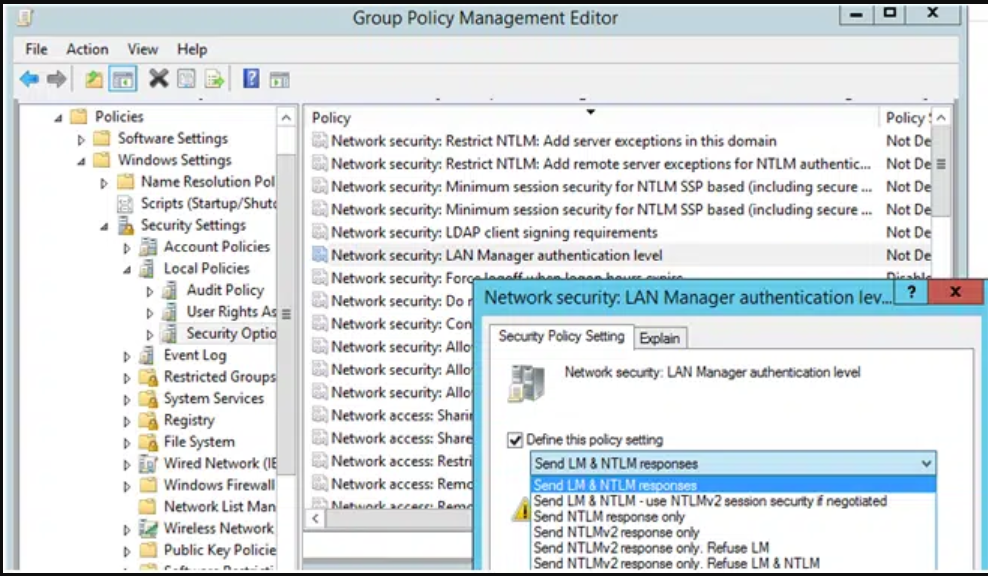
Network security LAN Manager authentication level
Make sure you set the correct authentication level. We have had cases where NTLM was forbidden globally