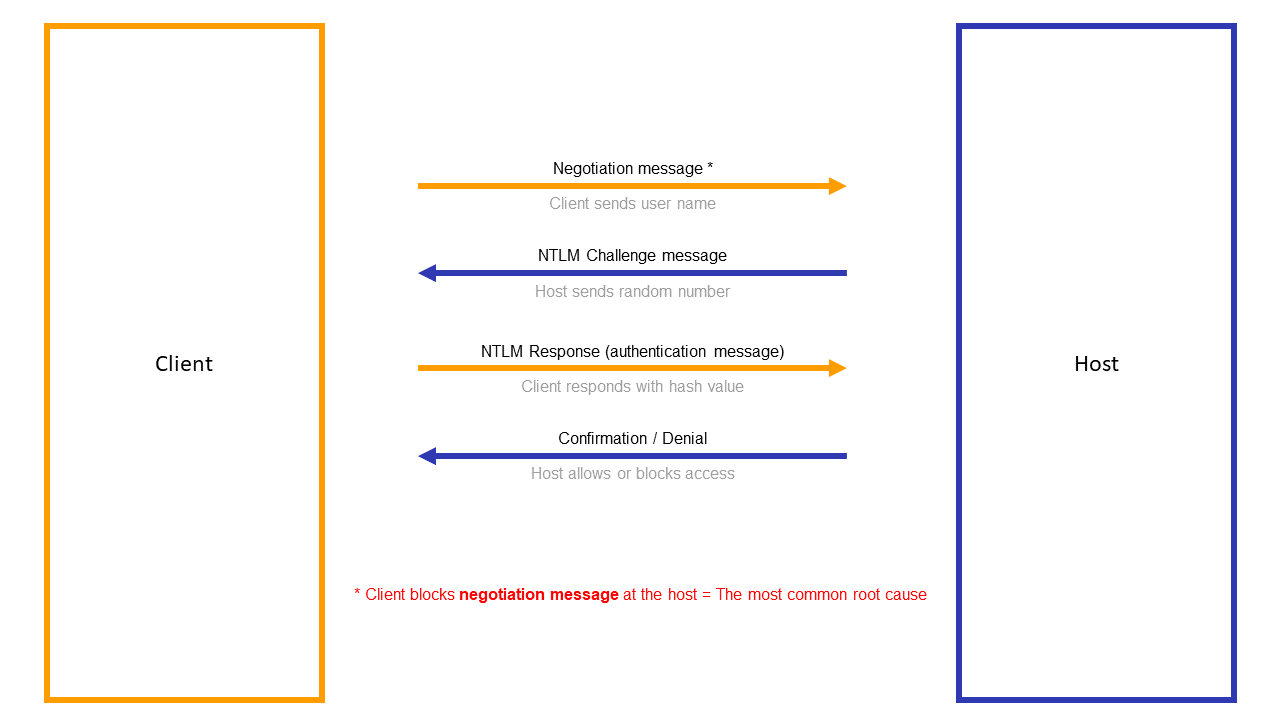
El envío de credenciales de Windows a través de la red puede ser leído potencialmente por terceros si la red no se ha protegido adecuadamente. Por este motivo, cualquier parte de este artículo que no forme parte de un archivo de configuración de DocuWare debe ser siempre aprobada y personalizada cuidadosamente por su departamento de seguridad.
Problema:
Sin embargo, siempre aparece la ventana de inicio de sesión de Windows. ¿Qué debe hacerse para autenticar a un usuario mediante NTLM?
Respuesta:
El propio DocuWare espera durante este proceso a que el host apruebe si el cliente puede ver el recurso o no.
NTLM sólo funciona de forma predeterminada para sitios de intranet, pero HTTPS no se reconoce como sitio de intranet por experiencia.
- Navegador
El navegador puede transferir el nombre de usuario de windows al host:
Ubicación: Ordenador del cliente
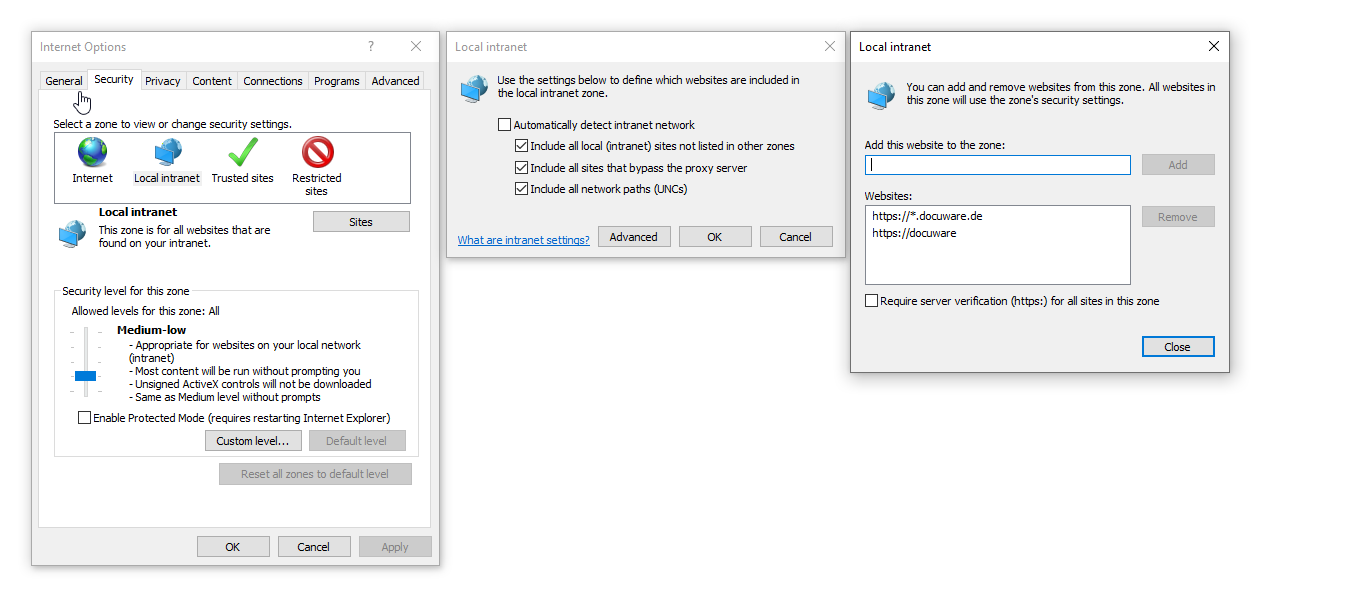
Edge, Chrome: (Opciones de Internet > Seguridad > Intranet local > Personalizar nivel: Autenticación de usuario - Inicio de sesión automático con nombre de usuario y Contraseña. Además, el sitio web de DocuWare (a*) debe añadirse a la zona de intranet local.
Ver captura de pantalla
Edge extra: De forma predeterminada, Microsoft Edge utiliza la zona de intranet como lista permitida para la Autenticación integrada de Windows (WIA). Como alternativa, puede personalizar la lista de servidores habilitados para la Autenticación Integrada mediante la política AuthServerAllowlist.
https://learn.microsoft.com/en-us/deployedge/microsoft-edge-security-identity
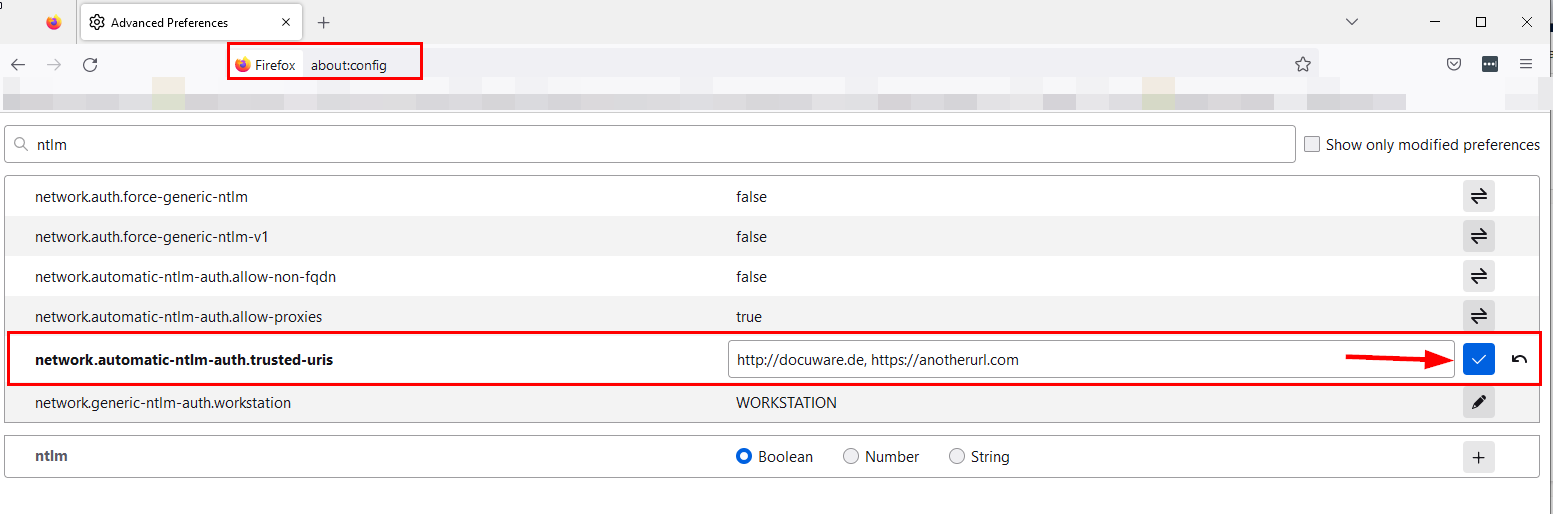
Firefox: about:config > network.automatic-ntlm-auth.trusted-uris > Aquí se introduce la página web de DocWare (a*).
Ver captura de pantalla
a* Para todos los navegadores: Aquí se introduce la URL con el protocolo. Si se llama a DocuWare a través de https://docuware.de/DocuWare, el valor es https://docuware.de. - Cliente
El cliente puede transferir el ID de Windows al host
Ubicación: Ordenador del cliente
Windows impide por defecto los ataques por reflexión=
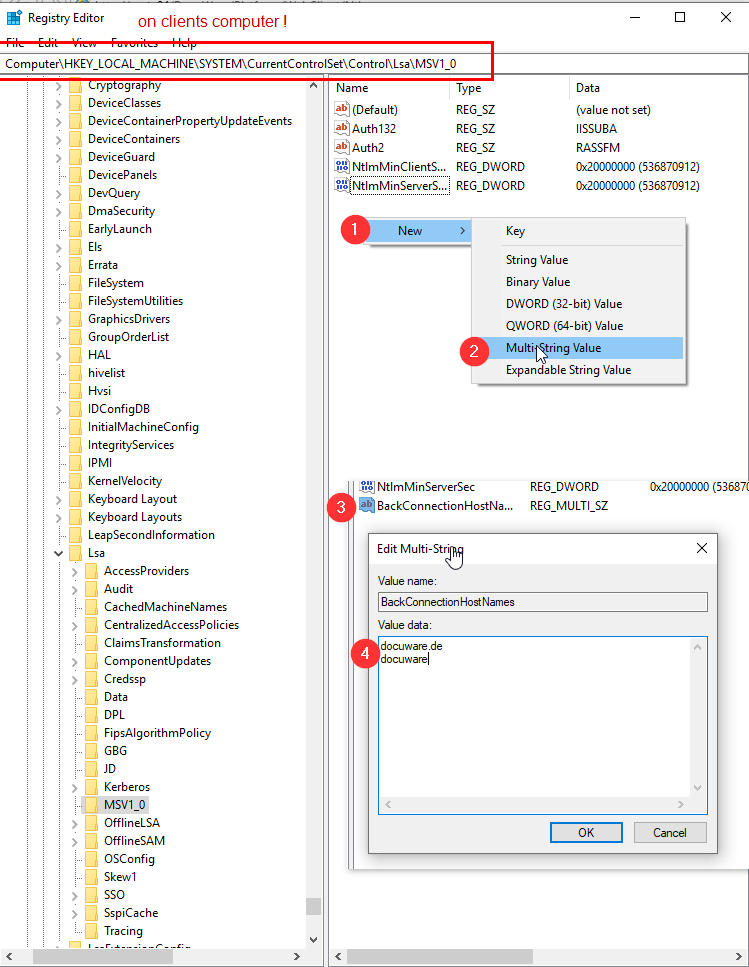
(b*) Debe introducirse una clave en el registro. Ésta define a qué host se puede transferir el ID de Windows.
Ruta del registro en el cliente: Computer\HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa\MSV1_0
Tipo de clave: valor multi-string
Nombre clave: BackConnectionHostNames
Contenido de la clave: Cualquier URL (sin protocolo https y sin ruta). Si se llama a DocuWare a través de https://docuware.de/DocuWare, el valor es docuware.de
Ver captura de pantalla - ID dered
El usuario de DocuWare tiene el ID de red correcto (ID de usuario de Windows)
Ubicación: /DocuWare/Ajustes/ - Proveedor de identidad
Se ha elegido NTLM como método de inicio de sesión SSO.
Ubicación: /DocuWare/Ajustes/
b* Le recomendamos que hable primero con su departamento de seguridad informática, ya que el envío de credenciales de Windows a través de la red puede ser inseguro. - SSO basado en WIA con ADFS
Para soportar SSO basado en WIA en Microsoft Edge (versión 77 y posteriores), es posible que también tengas que hacer alguna configuración del lado del servidor. Probablemente tendrás que configurar la propiedad WiaSupportedUserAgents de Active Directory Federation Services (AD FS) para añadir soporte para la nueva cadena de agentes de usuario de Microsoft Edge
Fuentes externas de información:
https://learn.microsoft.com/en-us/deployedge/microsoft-edge-security-identity
https://www.crowdstrike.de/cybersecurity-101/ntlm-windows-new-technology-lan-manager/ (alemán)
https://www.crowdstrike.com/cybersecurity-101/ntlm-windows-new-technology-lan-manager/ (inglés)
https://www.crowdstrike.com/ bus que NTLM para encontrar más artículos de blog de este sitio web
Captura de pantalla Intranetzone:
Captura de pantalla Clave del Registro:
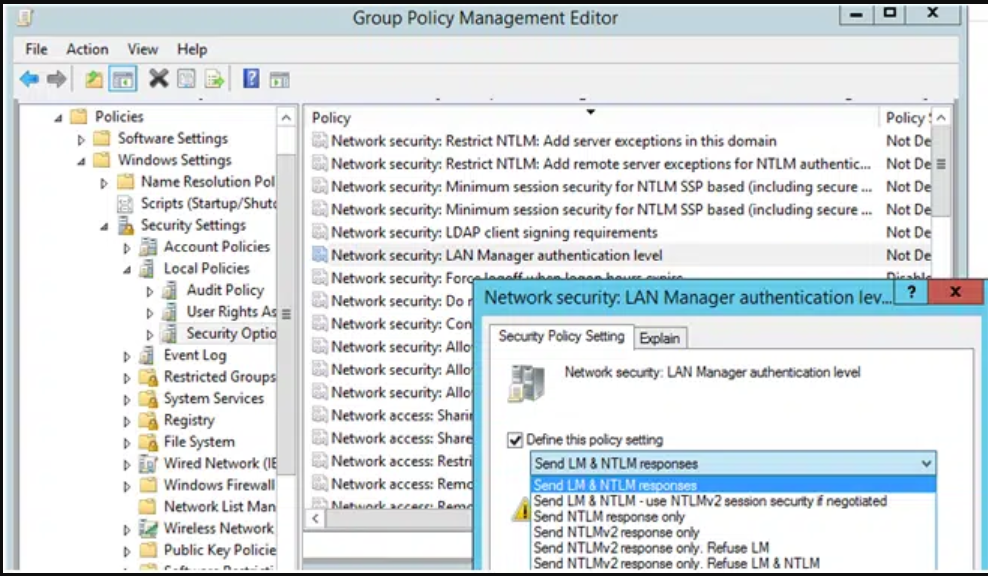
Network security LAN Manager authentication level
Asegúrese de establecer el nivel de autenticación correcto. Hemos tenido casos en los que NTLM estaba prohibido globalmente
Tenga en cuenta: Este artículo es una traducción del idioma inglés. La información contenida en este artículo se basa en la(s) versión(es) original(es) del producto(s) en inglés. Puede haber errores menores, como en la gramática utilizada en la versión traducida de nuestros artículos. Si bien no podemos garantizar la exactitud completa de la traducción, en la mayoría de los casos, encontrará que es lo suficientemente informativa. En caso de duda, vuelva a la versión en inglés de este artículo.